
5 Steps to Secure Communication Using Azure App Service and Azure SQL
When we design our architecture in Azure which involves database often we doesn’t catch one small detail. The default behavior of database service in Azure when come to traffic is to move all communication using public internet exposed endpoint. In other words our data is moved using public internet.
Private endpoints
But what is a private endpoint? According to Microsoft documentation it is
A private endpoint is a network interface that uses a private IP address from your virtual network. This network interface connects you privately and securely to a service that’s powered by Azure Private Link. By enabling a private endpoint, you’re bringing the service into your virtual network.
Basically this is a private IP address received from our Virtual Network which we can use for connection to one of many services like:
- Azure Storage
- Azure Cosmos DB
- Azure SQL Database
- Your own service, using Private Link service.
As last point mention we can even use own service for connection such example will usage of Azure Data Factory which connects to on-premises database servers using Managed Virtual Network and Private Link Service.
Secure communication in 5 steps
So we have an application architecture like on below diagram which is a most common and simple approach when we deploy application to Azure.
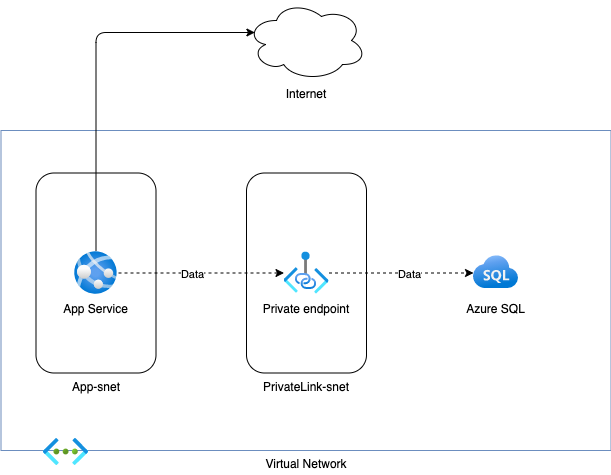
What services do we have here:
- Azure App Service as compute platform which utilize Standard tier for production workload
- Azure SQL as database where we store our relational data
Step 1 - Creation of VNET and Subnets
As first step we should create in our Resource Group a new Virtual Network and at least two subnets. In my sample I create VNET adv001-vnet with address range 10.0.0.0/20. In this VNET I have two subnets adv001-app-snet and adv001-private-snet into this subnet I will add my Private Endpoint interface later.
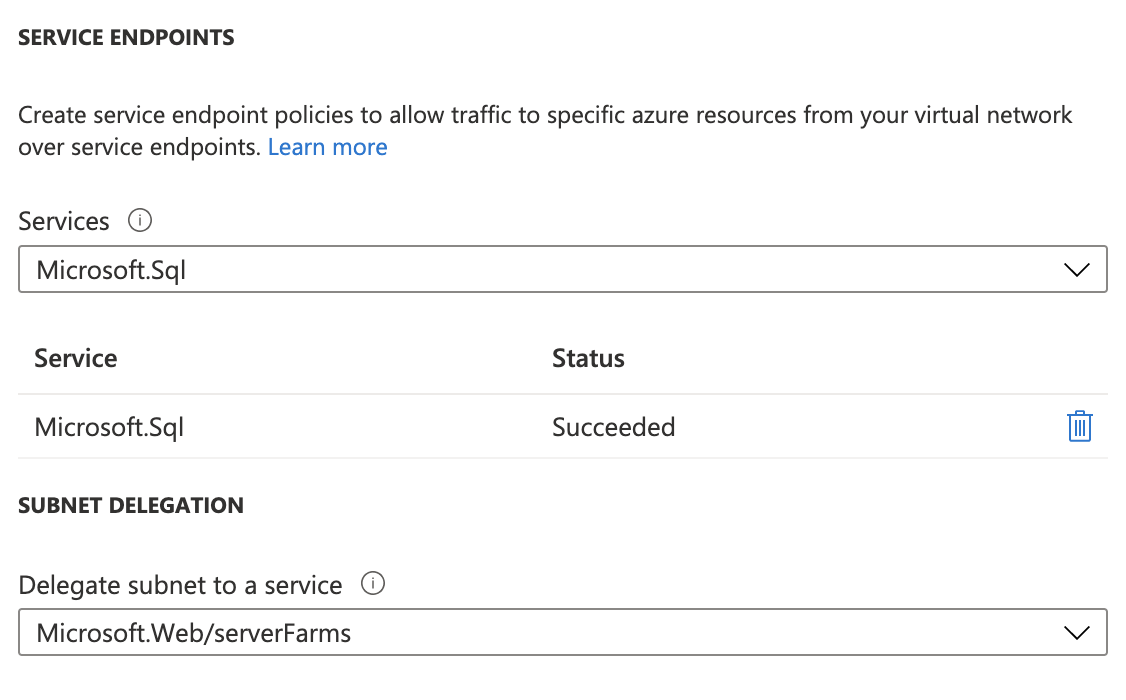
In application subnet adv001-app-snet we should remember on Service Endpoint to Microsoft.Sql
As @mgrabarz mention Service endpoint is not required in this scenario when we are using Private Link. Maybe it is worth it to write comparison between Service Endpoints & Private Link in context of App Service.
Step 2 - Change Network settings on Azure SQL
We need to disable feature All Azure services for our Azure SQL instance. This setting blocks all communication from Azure services using public endpoints of DB server.
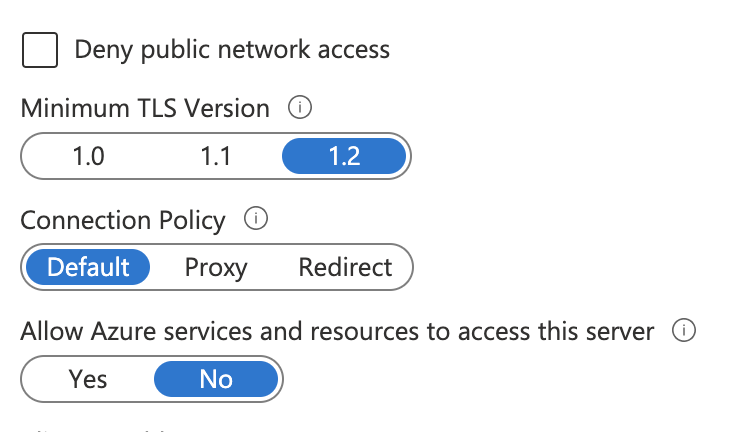
Under Private endpoints connection tab we need to create a Private endpoint connection with Private DNS Zone. This interface should be created in subnet adv001-private-snet.
Step 3 - App Service Standard tier
To have an option to use App Service VNET integration and use Private interface which we create in previous step we need to Scale up to one of Production tiers.
Step 4 - App Service VNET integration
App Service integration with a VNET is a quite simple task we need only to remember about few settings Route All and select correct subnet which is in our case adv001-app-snet.
Route All setting give us solution how App Service resolves DNS name to Private Interface IP of our Azure SQL instance.

Step 5 - Use of contained user or managed identity
To secure our database we have two options use of contained user
Contained user access to contained databases - SQL Server
Another option even more secure is to use Managed Identity and authorize our DB use using Azure AD
Tutorial: Access data with managed identity - Azure App Service